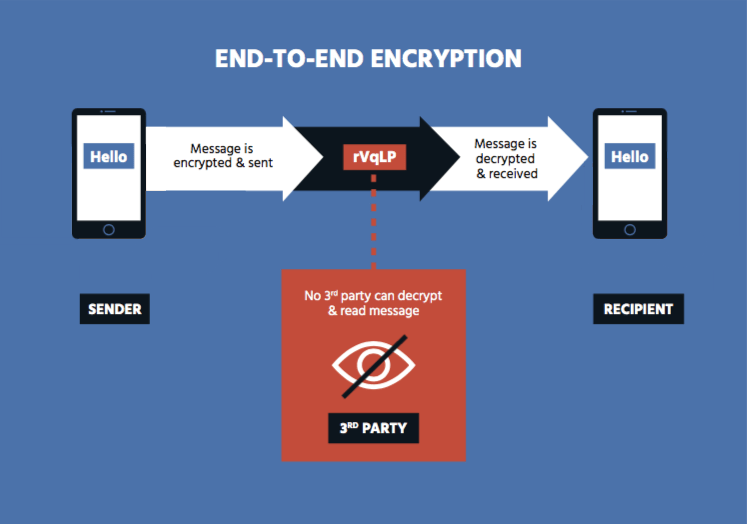
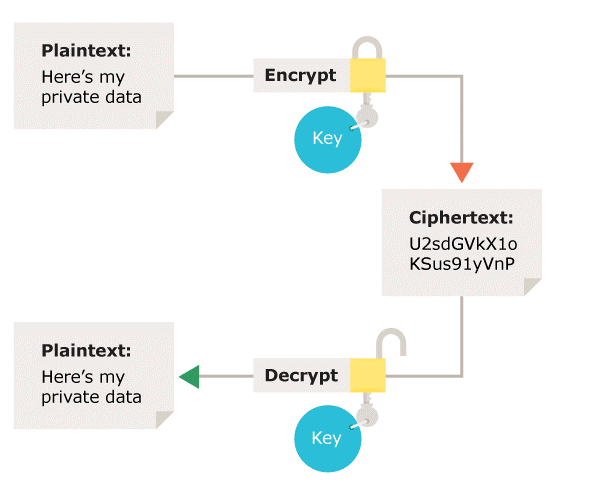
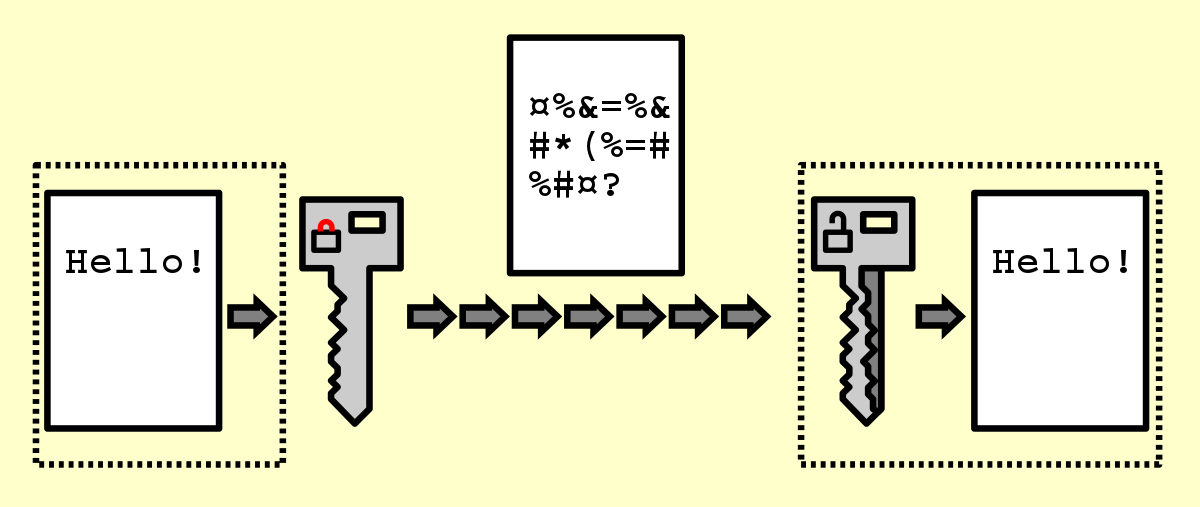
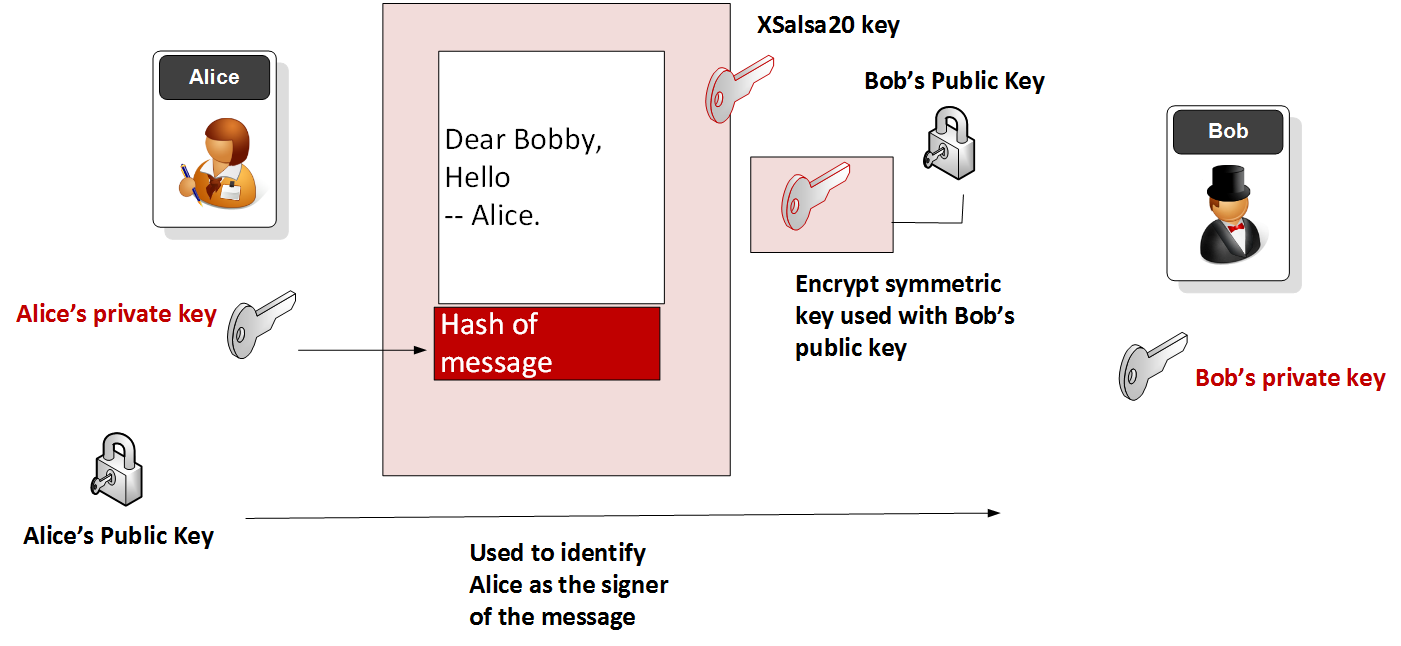
GitHub - magiclen/js-short-crypt: ShortCrypt is a very simple encryption library, which aims to encrypt any data into something random at first glance.

Design and Implementation of End to End Encrypted Short Message Service (SMS) Using Hybrid Cipher Algorithm

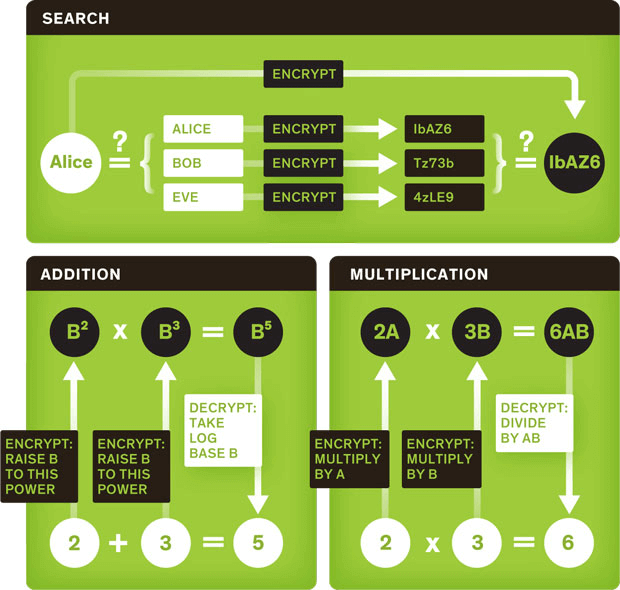

![PDF] Fast Keyword Search over Encrypted Data with Short Ciphertext in Clouds | Semantic Scholar PDF] Fast Keyword Search over Encrypted Data with Short Ciphertext in Clouds | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/ac4bf8ba86231775f88e22f844392501fa337403/4-Figure1-1.png)