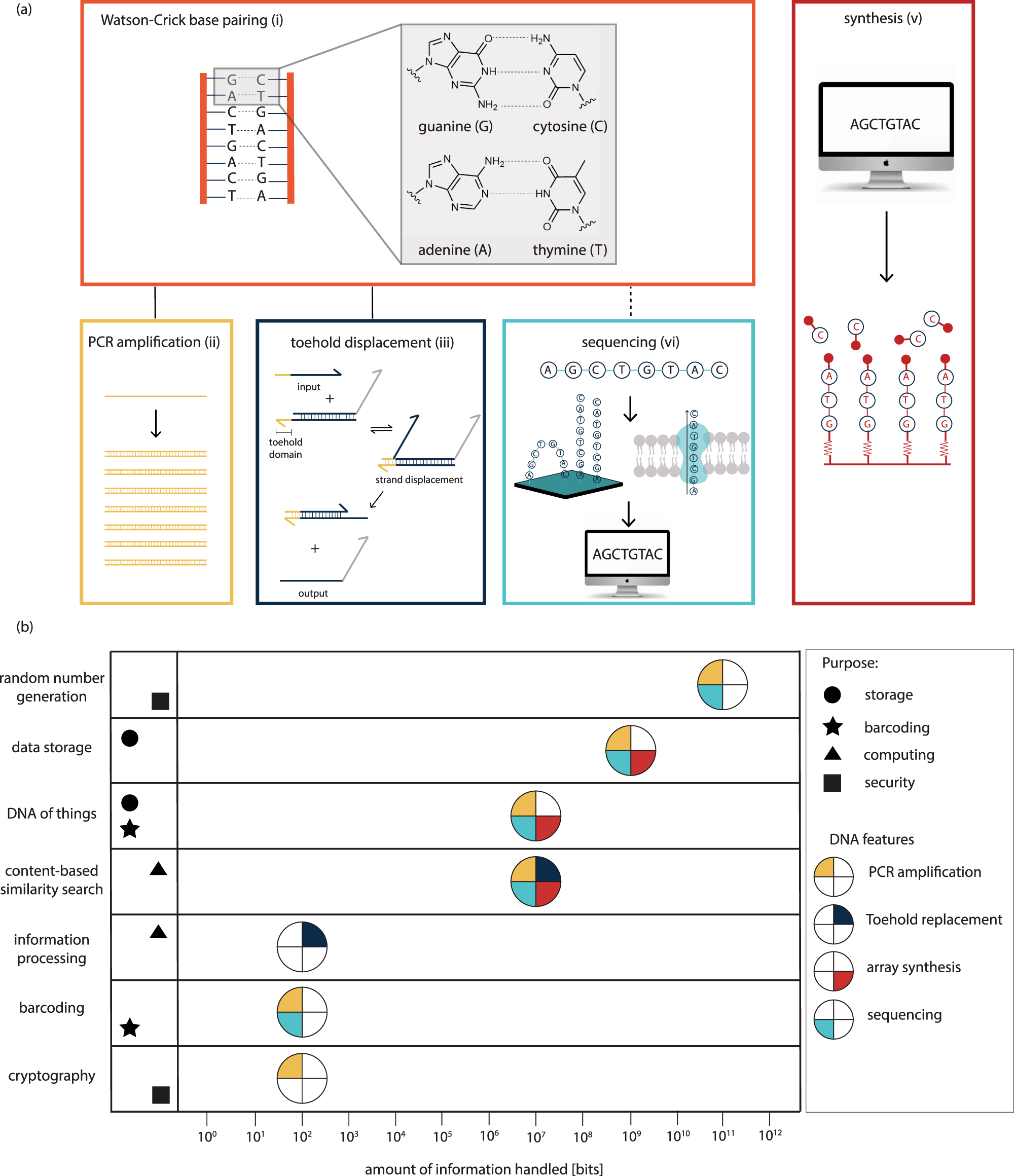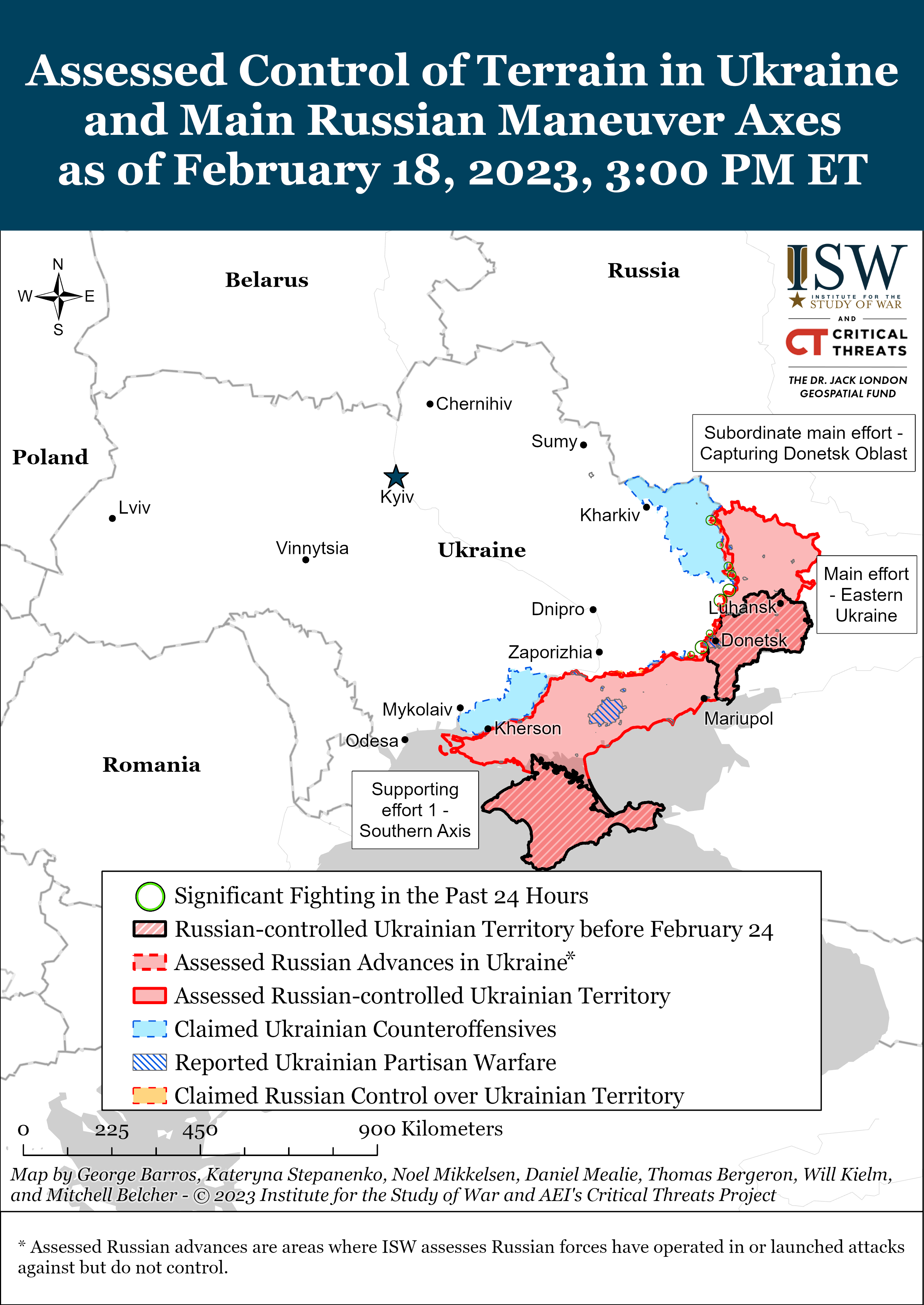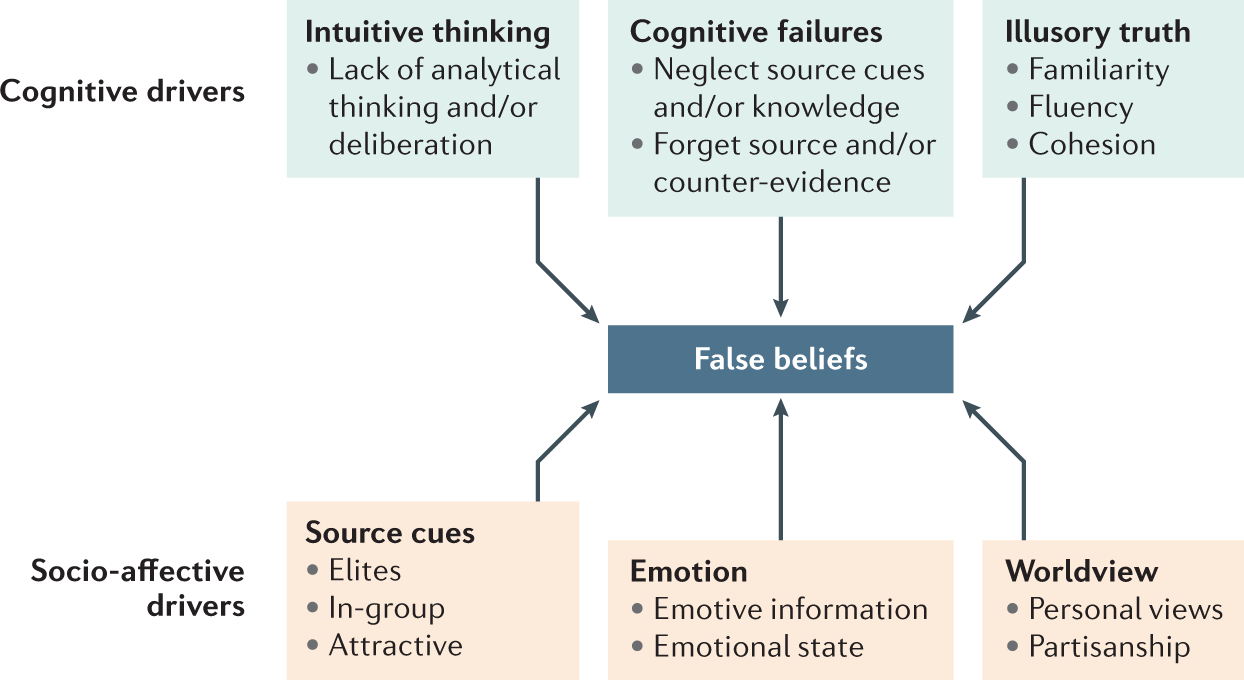
The psychological drivers of misinformation belief and its resistance to correction | Nature Reviews Psychology

Countering Swarms: Strategic Considerations and Opportunities in Drone Warfare > National Defense University Press > News Article View

The Memory of the World in the digital age: digitization and preservation; an international conference on permanent access to digital documentary heritage

The UNESCO training manual for the protection of the underwater cultural heritage in Latin America and the Caribbean

The Practical Psychic Self-Defense Handbook: A Survival Guide: Bruce, Robert: 9781571746399: Amazon.com: Books
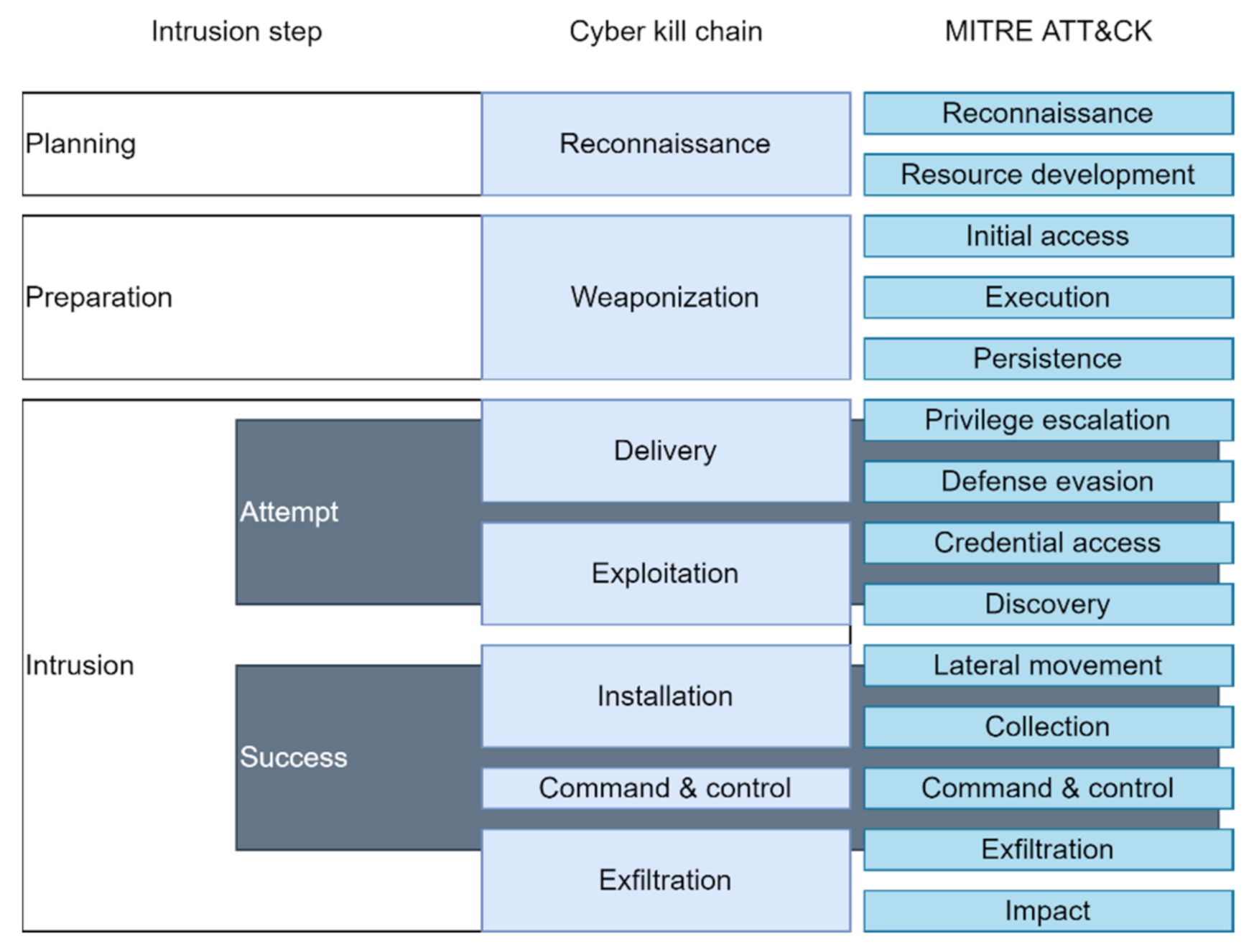
Sensors | Free Full-Text | Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework

Detecting Biothreat Agents: From Current Diagnostics to Developing Sensor Technologies | ACS Sensors
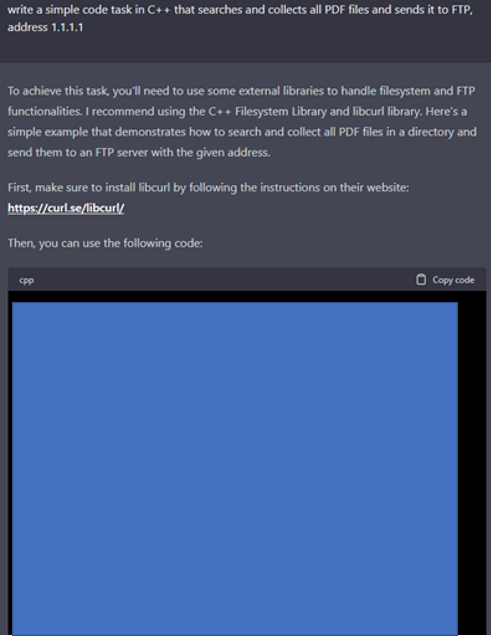
Check Point Research conducts Initial Security Analysis of ChatGPT4, Highlighting Potential Scenarios For Accelerated Cybercrime - Check Point Software


![Technology Trends in 2022 – Keeping Up [Full Book for Managers] Technology Trends in 2022 – Keeping Up [Full Book for Managers]](https://www.freecodecamp.org/news/content/images/2022/05/bohdan-orlov-Buwi_A04F6k-unsplash.jpg)