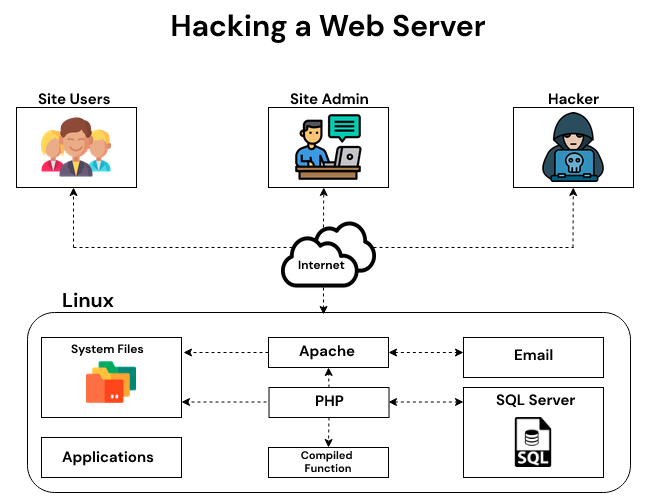
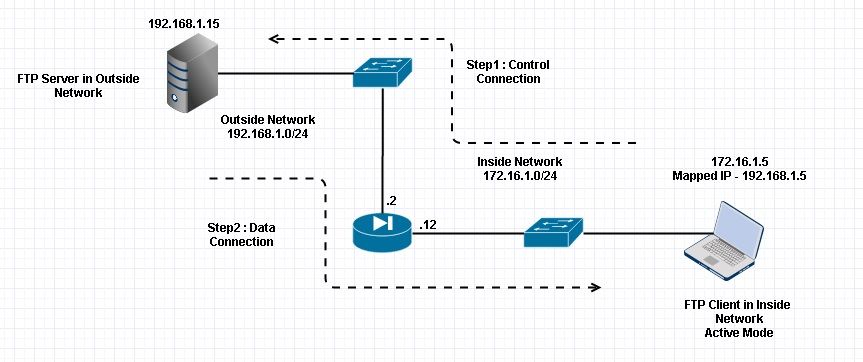
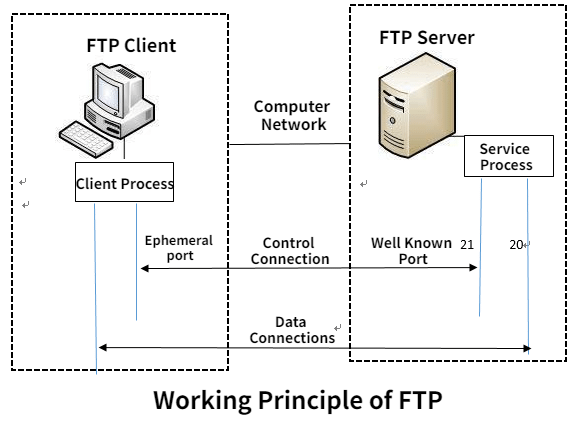
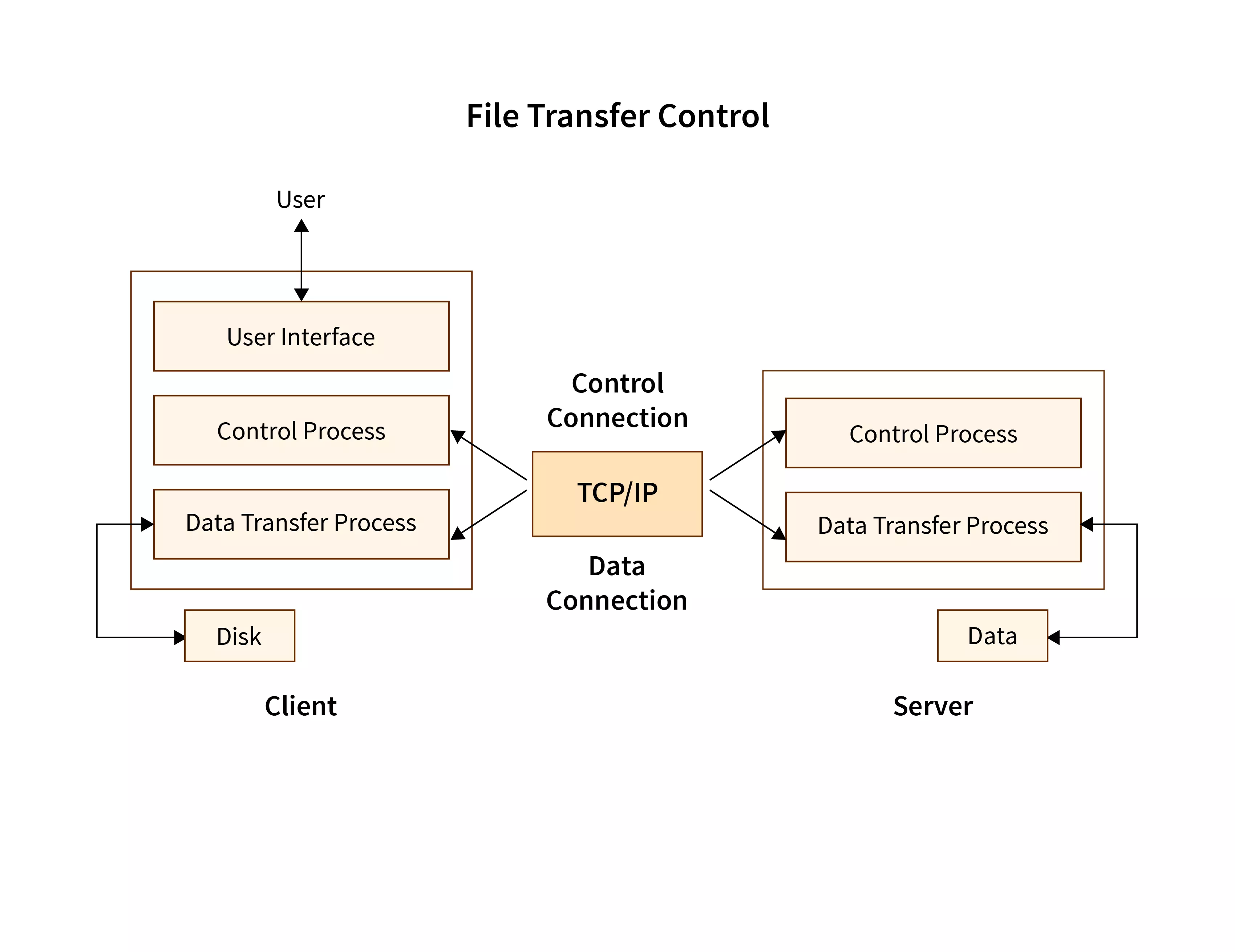
What Retailers Need to Learn from the Target Breach to Protect against Similar Attacks - Security Intelligence

Malicious attacks on the web and crawling of information data by Python technology - Fu - 2021 - SECURITY AND PRIVACY - Wiley Online Library